Usernames, passwords of bank, government, healthcare workers compromised

Thousands of employee usernames and passwords from government departments, local banks, and healthcare organisations in New Zealand have been leaked to the dark web, a new cybersecurity report claims.
Findings from nWebbed's NZ Cybersecurity Study found more than 18,000 government workers, 3,200 banking staff, and 2,000 healthcare organisation accounts with access to sensitive information have been detected on the dark web.
The dark web is a part of the internet that is not indexed by standard search engines, and may be used as an illegal marketplace by criminals.
"We are seeing widespread exposure of compromised credentials linked to core parts of the New Zealand economy, including health providers, government agencies, banks and large-scale businesses," said Julian Wendt, founder of nWebbed Intelligence, in a statement.
According to nWebbed's report, the compromised credentials are linked to more than 198,000 New Zealand companies and entities.
"These are trusted institutions that Kiwis interact with every day, and they are real emails and passwords sitting in the wild," Wendt said.
Wendt said the findings indicate how organisations in New Zealand underestimate cyber risks.
"In reality, our companies are being targeted every day, often because we're seen as a soft entry point into larger international networks," he said.
"Nearly half of the Fortune 500 companies worldwide have exposed employee credentials available online, and Kiwi companies are facing similar threats."
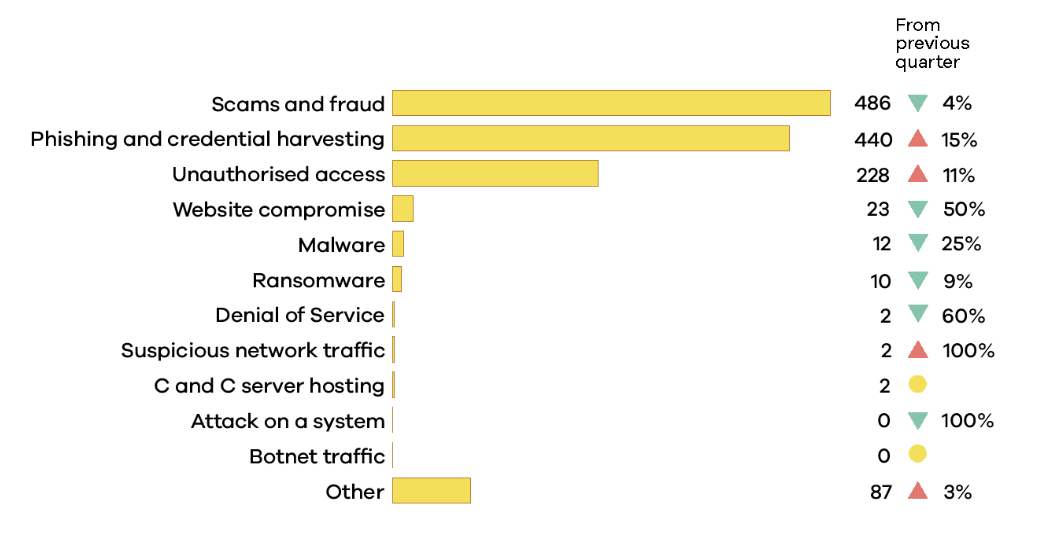
The National Cyber Security Centre (NCSC) recorded a total of 1,369 cyber security incidents in the first quarter of 2025.
Among them, there were 440 cases of phishing and credential harvesting, up 15% from the previous quarter, and the second-most reported type of incident.
Wendt warned that credentials harvested can remain online even after a hacking incident, waiting to be exploited.
"In some cases, we've seen attackers move within minutes of credentials appearing online," he said. "What starts as a single leaked password can escalate into a live intrusion before an organisation even realises there’s been a breach."
To address the problem, Wendt urged organisations to move away from reactive cyber security practices.
"You can't wait for the ransom note to start caring about where your data ends up. We need a preventative model, and that starts with visibility," he said.
He further called on organisations to treat external digital hygiene as seriously as they do internal firewalls.
"Most organisations are watching their perimeter, not what's already leaked. But if your staff credentials are out there, especially admin or technical roles, then attackers already have the keys."